Recently, "Cyber" companies emerged like mushrooms after the rain, making the process of choosing the most suitable product or service, complex or even impossible. In addition, threats and regulations are constantly evolving causing CIO, CISO or IT Infrastructure managers to focus on Information Security risk management.
I would like to share our Information Security consulting experience derived from dozens years of work in over 200 customers covering cyber products and services selection process while managing information security risks in aspects of necessary vs. recommended (or advised).
Cyber threats, as perceived in the last decade, are a wide scale Information Technology threats, originating, in most cases, from the organization's external perimeter (Internet, partners and suppliers), are premeditated, target focused and carried with high level of sophistication and magnitude. These threats aim to take hold over the organization's critical business assets and may danger as much as its mere existence.
Some claim, rightfully in our opinion, that an organization that maintains proactive Information Security routines, significantly reduces or even prevents the majority of cyber threats and that both building blocks are similar. Having said that and in light of the critical affect cyber threats could impose on an organization, we regard Cyber Defense as a separate topic with its own set of activities and technology adoption that requires a structured and prioritized work plan based on a proven methodology.
One of our key customers, an organization bound to enhanced Information Security regulation, has reached the conclusion that the time he is required to invest in "Cyber", whatever this term means, is too expensive, therefor he decided to use our Information Security experts and follow these methodology principles:
- Define the cyber threats and threat scenarios specific to the organization
- Perform a cyber threat survey
- Prepare a prioritized work plan
- Follow and manage the work plan's execution
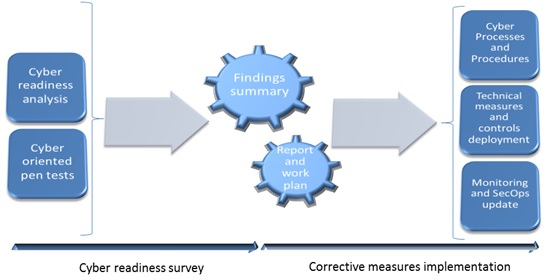
Stage 1 – Organization's specific cyber threats and threat scenarios
The objective of this stage is to form a map of cyber oriented potential threats and attack vectors in reference to the critical information assets. Every source of information, written or verbal is evaluated in the context of a cyber-attack in order to define its probability. For example, the threat potential of an asset such as a data base which contains credit card numbers and is connected to an online front end application is considered "High". This stage is mainly carried out by reviewing existing material (relevant penetration tests, information assets map etc.) and by interviewing key personnel.
Stage 2 – Cyber threat survey
Based on the threat outline, we define a set of infrastructure level penetration tests (network, servers, end points etc.) application level penetration tests (Database, Web applications etc.) and a "human" level penetration test (a tailored phishing scam scenario). Many organizations that already manage Information Security perform various tests, therefor the defined activity complete the analysis of these existing penetration tests. The collection of tests is designed on one hand to evaluate how easy/difficult it is to execute a cyber-attack and on the other hand to assess the existing identification mechanisms and to simulate cyber events' operational response processes. At the end of this stage, a cyber-attack probability factor is added to stage 1 analysis. In addition, this stage records the efficiency of the data security products, the monitoring tools (if exist) and the processes/drills with regards to detecting, alerting and reacting to the simulated cyber-attacks.
Cyber Readiness Stages Diagram
Stage 3 – Prioritized work plan
This stage starts with the validation of the findings and their analysis followed by a preparation of a prioritized work plan draft designed to increase the efficiency of the organization's cyber defenses and also to establish a cadence of continuous improvement in its cyber readiness. The work plan will include topics such as: Information Security Management System (Information assets, policy, procedures, processes, controls etc.), technology (OS hardening, network, access controls, security products configuration and more), employee's awareness improvement, business continuity, complimentary security technologies etc.
Stage 4 – Management of gap mitigation execution
It's Fixi'n time! Whether managed by the organizations' CISO or provided by IPV Security's CISO-as-a-Service, the approved and budgeted work plan, whole or partial, is ready for execution. IPV Security helps customers manage this stage using a project framework with KPIs and SLA. The project includes: ensuring each and every gap is addressed – technical or procedural and the characterization of security products, from initiation stage to final operation stage (including a professional unbiased evaluation of the supplier). The project is delivered by our cyber consulting experts while ensuring the integration between the relevant parties within the organization (IT, HR, O&M etc.), in a flexible engagement model.
Conclusion
To summarize, the current cyber companies' flood will eventually pass but ensuring an organization's Information Security and implementing the correct measures to guaranty confidentiality, integrity and availability of its critical business assets, requires a combination of a structured methodology and proven expertise.
We welcome you to a professional cyber consulting meeting, in which we will be able to learn the unique requirements of your organization and evaluate how our experience and insights can help you reduce Information Security and Cyber Defense risks!


